IT Security Processes | Anatomy of Ransomware
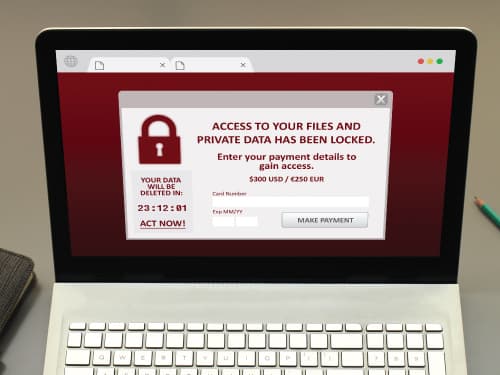
Ransomware is a type of malware that threat actors use to infect computers and encrypt computer files until a ransom is paid. After the initial infection, ransomware will attempt to spread to as many connected systems as possible, including file systems and other accessible systems on a business’s network.
To avoid becoming a Ransomware victim, businesses should take actions that include putting security processes in place to ensure your IT environment is fully protected. Leveraging the Center for Internet Security’s (CIS) Critical Security Controls (CSC) is a solid place to start. These same security processes will help protect your critical business environment from malware, which accounts for nearly 30% of all breaches, according to Verizon’s 2019 Data Breach Investigations Report. In addition, the evaluation portion of the CSC is included with OneNeck’s virtual CISO (vCISO) service.
Mitigating contact with malicious web sites and emails.
Typically, the initiating step of a security breach is attributed to end users, where they have visited a malicious web site or acted unknowingly on a malicious email. There are several key security processes that can mitigate this initiating event:
- Implement a Security Awareness and Training Program (CSC Control #17). This includes training the workforce on how to identify different forms of social engineering attacks (e.g., phishing, phone scams and impersonation calls). Educate your workforce to:
- Use caution with links and when entering website addresses.
- Check a website’s security (look for the lock) to ensure the information you submit is encrypted before you provide it.
- Know email senders.
- Open email attachments with caution.
- Continuous Vulnerability Management (CSC Control #3). Deploy automated software update tools in order to ensure the operating systems are running the most recent security updates provided by the software vendor. Typically the malware—and therefore attackers—are going to leverage a known vulnerability in an operating system to gain access or take control of a system.
- Malware Defenses (CSC Control #8). End point protection needs to be implemented on all workstations and servers. Advanced Threat Protection can detect, stop the movement of, or control the execution of malicious software. Additionally, it is best to be centrally managed to ensure:
- End point software is at current versions.
- It is scanning appropriately.
- A notification process is in place for when the Advanced Threat Protection detects and takes action.
- Quarantined files are handled properly.
If malware takes hold, defenses that can help.
If the malware is successful in taking hold in your IT environment, there are several defenses that can help prevent the malware from evolving into a full-scale ransomware event:
- Boundary Defense (CSC Control #12). The primary device involved is your firewall; however, critical to the firewall are features available (IDS/IPS), the architecture (configure DMZs, segmentation), the configuration you’ve implemented (put in filters for outbound traffic), and regularly scan your firewall to assure you’re only allowing what you want. When malware is installed it typically wants to talk to a bad actor outside your network; therefore, if your firewall is configured properly, it can prevent malware from being able to connect back to the bad actor.
- Controlled Use of Administrative Privileges (CSC Control #4). Configure systems to issue a log entry and alert when an account is added to or removed from any group assigned administrative privileges. One of the primary goals of malware is to gain full access to your environment, and the best way to do that is for the bad actor to compromise a privileged account, such as Domain Admin.
- Monitoring/Logging (CSC Control #6). Ensure appropriate logs are being aggregated to a central log management system for analysis and that they are being reviewed. Poor or nonexistent log analysis processes can allow attackers to control victim machines for months or years without anyone in the target organization knowing, even though the evidence of the attack is being recorded—in unexamined log files.
If the worst happens—and you are prepared—you still do NOT have to pay the ransom.
If the bad actor has taken hold, it’s not good—but all is NOT lost. While it’s likely the bad actor has gained access to a privileged account in the environment and your critical data is at risk, at this point, you can still minimize the impact.
- Incident Response and Management (CSC Control #19). Quickly discovering an attack and then effectively containing the damage, eradicating the attacker’s presence and restoring the integrity of the network and systems. This is a critical step—ensuring you inspect your entire environment for any movement the bad actors might have made. Otherwise, if you just move to recovering your environment, the bad actor will return quickly.
- Data Recovery Capabilities (CSC Control #10). Ensure each of the organization’s key systems are backed up as a complete system to enable the quick recovery of an entire system. The challenge with ransomware is that if the initiating event took place weeks/months earlier, your backup data may already be suspect. This is precisely why, when implementing your backup systems, you have to ensure all backups have at least one backup destination that is not continuously addressable through operating system calls, so that the ransomware can’t directly encrypt files.
Typically, there are several events that happen over the course of days, weeks or months that ultimately result in a ransomware attack. While there are a wide number of variants for ransomware, most events follow the path laid out above. Every step in the process could be identified and addressed. It can be a long journey, but you don’t have to go it alone. Through partnership with OneNeck’s vCISO service, the CSC will be leveraged to help assure your IT environment is protected.
Additional Resources:




