Is My Password as Safe as I Think It Is?

Password Security Challenges
Passwords have long been the leading method of authentication and protecting sensitive information. However, as technology advances and the sophistication of cyber threats continue to evolve rapidly, the security of passwords is critical. Everyone must ask, “Is my password as safe as I think it is?”
The principal issue with passwords is that they can be easily compromised. Hackers use various techniques to obtain passwords, including socially engineered phishing attacks, keyloggers, and dictionary attacks. Additionally, many users employ weak, easily guessable passwords, some of the most common being “123456”, “password,” or “guest.” Using unsafe passwords makes it easy for hackers to access accounts and steal sensitive information.
Another challenge of passwords is that if users forgo short and obvious passwords, they often run into the issue of password retention. Everyone has multiple accounts and passwords, and it can be challenging to keep track of them all. As a result, people often reuse passwords across multiple accounts or write them down (monitor sticky-note, anyone?), thus compromising security.
Finally, even when following best practices, there are still risks concerning the security of password databases. If an organization’s password database is hacked, all of its users’ passwords face the potential of being exposed. These breaches have occurred in several high-profile instances, compromising millions of passwords and associated user ids.
So, are passwords as safe as most users think they are? Probably not. While passwords certainly provide some level of protection, they are not infallible, especially on their own. However, everyone can employ several tips and strategies that vastly decrease the likelihood of their accounts being compromised.
Ways to Protect Your Passwords
It should come as no shock that strong and unique passwords are safer and more challenging to crack. Even with this knowledge, many individuals still fail to put it into practice consistently. Length, complexity and account separation are all crucial factors to consider when creating strong passwords.
Password Length–
The length (total number of characters) is one of the essential aspects of password effectiveness. At its most basic, longer passwords are more difficult to crack because they have a larger number of possible combinations. Thus, it is harder for an attacker to guess the correct password through a “brute force” attack, which systematically tries many combinations of characters to guess a password. The attacker uses software to automate the process of trying different combinations and often starts with the most commonly used characters or words. More sophisticated brute force attacks can also include “password dictionaries,” lists of words and phrases of the most widely used passwords.
Each character increase in the length of a password exponentially adds to the possible combinations a brute force attack must try to compromise that password successfully. The generally accepted minimum password length by cybersecurity experts is 14 characters. A 14-character password made up of random letters and numbers has possible combinations of approximately four quadrillion (yes, with a “q”). The sheer volume of possible combinations significantly fortifies passwords against brute-force attacks.
Password Complexity–
A second vital aspect of password effectiveness is complexity. Ultimately complex passwords are more difficult to crack than simple ones and thus provide a more robust level of security. A complex password includes a mix of characters, such as uppercase and lowercase letters, numbers, and special characters – including spaces when permitted. Using a mixture of characters vastly increases the number of possible combinations.
Another reason why complexity is essential is that it makes it harder for an attacker to use the aforementioned “dictionary” attack. If your password is a complex, unique and random string, it is not likely to be found in the attacker’s pre-computed list. This complexity also makes it difficult for anyone, even individuals in direct contact with a user, to deduce or guess a password.
Password Separation–
Using separate passwords for different accounts is vital for security as it reduces the risk of compromising multiple accounts if a password is stolen or otherwise obtained by an attacker. If the same password is used for multiple accounts, and an attacker can obtain that password, they potentially have access to all associated accounts. Breaches like this can be particularly problematic if one of the accounts is sensitive, such as an organizational or financial account.
If an attacker obtains a password, when using separate passwords for all accounts, the attacker will only be able to access the account associated with that password. They will not be able to access any other accounts, limiting the damage they can do. This separation of passwords keeps individuals protected against automated attacks called “credential stuffing,” where attackers use lists of stolen usernames and passwords (often from another data breach) and try them on a variety of accounts (emails, credit cards, businesses, etc.). Using a unique password for each account reduces the possibility of a compromised password having a far-reaching negative impact.
How Long Does it Take to Crack a Password?
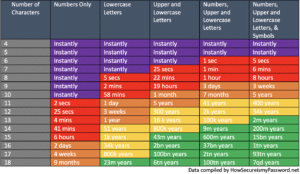
Here is an excellent visual representation that illustrates the above concepts. It shows how long, via today’s modern computing power, it takes for brute force attacks to crack passwords of various lengths and complexity. Many public email providers require a minimum 8-character password, which, even when using a combination of numbers, upper and lowercase letters and symbols, can be cracked in 8 hours—increasing this by one character ups the total to 3 weeks. Utilizing a password with 14 characters raises the estimate to 200 million years!
Creating a Strong Password
To review, a password must be long (preferably at least 14 characters) and complex (including numbers, letters, symbols and spaces when permitted). Additionally, each account should have a unique password. Since the average person has dozens of accounts, keeping track of and managing passwords can be challenging. There are recommended strategies to incorporate and some things to avoid that benefit not only strong password creation but also organization.
- Don’t use obvious details as passwords. Family members or pets’ names are among those most commonly associated with passwords. While variations of these names may be simpler to remember, this information is generally easy to find online as open-source intelligence (OSINT) and result in readily compromised passwords. The same holds for important dates (birthdays, anniversaries, etc.) and locations (addresses or hometowns).
- Instead of passWORDS, think more in terms of passPHRASES. Passphrases are typically longer than passwords and, therefore, harder to crack. A passphrase made of multiple random words can be more difficult to guess than a shorter, alphanumeric password, even if the password is considered complex. As with passwords, combinations of uppercase and lowercase letters, special characters and numbers are recommended.
Additionally, passphrases are often more memorable than random strings of characters, making it less likely that the user will have to write the passphrase down or store it in an unsecured location. They can also be harder to steal through phishing or social engineering tactics because, in most cases, they don’t contain personal information.
- Password managers are a great way to keep track of login credentials. These tools use encryption to store and generate complex passwords for all online accounts. Additionally, they are configurable to fill in login information automatically, eliminating manual entry of usernames and passwords. Thus, logging into accounts is more convenient and secure by making it less likely for accounts to be vulnerable via weak or reused passwords. Another benefit of password managers is minimizing exposure to phishing attacks. If a user unknowingly clicks a bad link, the password manager will not offer to fill in login credentials because it does not recognize the imposter website.
- Finally, whenever possible, use multi-factor authentication (MFA). MFA makes it considerably more difficult for attackers to gain unauthorized access to an account, even when they have access to an account password. MFA can help defend against phishing, keyloggers and malware attacks by requiring the attacker to steal or replicate a second factor (e.g., a phone) to pass the MFA check. Security in layers is a best practice, and while not foolproof, MFA provides an additional layer of security that can significantly reduce the risk of unauthorized access to your accounts.
OneNeck – A Security Partner You Can Trust
As an experienced IT security services provider, OneNeck is here to help. Our team can assess your current security posture, develop a defense strategy, and help you better leverage your existing security investments. Contact us today to speak with a OneNeck security professional.
Frequently asked questions…
What is the safest way to protect passwords?
The safest way to protect passwords is to use a strong, unique password for each account, and to store them securely using a password manager. A password manager encrypts and stores your passwords, making them accessible only with a master password or biometric authentication, and can generate strong, random passwords to help ensure maximum security.
What is a passphrase?
A passphrase is a series of words or other text used as a password or key to protect access to an account, device, or other resource. Passphrases are typically longer and more complex than traditional passwords, and can be easier to remember while also providing greater security against brute-force attacks.
Do security experts recommend password managers?
Yes, many security experts recommend using password managers as a secure way to manage passwords. Password managers can generate strong, unique passwords for each account, store them securely, and automatically fill them in for you, reducing the risk of password reuse, weak passwords, and other security issues. However, it’s important to choose a reputable password manager and follow best practices for password security, such as using multi-factor authentication and regularly changing passwords.
What is the difference between 2FA and MFA?
2FA stands for “two-factor authentication,” which requires users to provide two forms of authentication to access a resource, typically a username/password combination and a one-time code sent via SMS or generated by an app. MFA, or “multi-factor authentication,” is a more advanced form of 2FA that requires additional forms of authentication, such as a fingerprint or facial recognition, in addition to the traditional username/password and one-time code.
Additional Resources:




