GLBA Audit for Educational Institutions

What the GLBA Audit Includes and How to Navigate the Pre-Audit Process
The Gramm-Leach-Bliley Act (GLBA) is longstanding United States law that includes provisions protecting the privacy of consumers’ financial information. The GLBA applies to all institutions offering consumers financial products or services. The U.S. Department of Education Federal and Student Financial Aid Office has asserted that Title IV Institutions of Higher Education are considered “financial institutions” and thus subject to the GLBA.
In October 2021, the FTC announced revised provisions of the Safeguards Rule requiring non-banking financial institutions, such as institutes of higher education, to develop, implement and maintain a comprehensive security system to keep their customers’ information safe.
Successfully enacting these provisions is critical for passing a GLBA audit. Initially set to take effect on December 9, 2022, a six-month extension was granted, pushing the deadline to June 2023.
Safeguards Rule
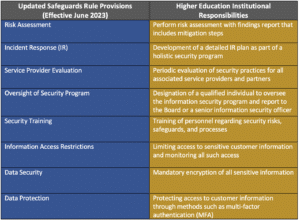
The Safeguards Rule instructs organizations to implement administrative, physical and technical protections as safeguards against cyberattacks, email spoofing, phishing schemes and similar cybersecurity risks. These provisions are where educational institutions will likely struggle to achieve and maintain compliance. Identifying and assessing risks, developing and maintaining an information security program and creating detailed incident response plans are a heavy drain on time, staffing and a school’s limited resources. Obtaining outside assistance in these areas is often a necessity.
GLBA Audit for Educational Institutions
With the June deadline fast approaching for institutions of higher education, it is imperative that schools not only understand what provisions auditors are examining but also how to prepare for the GLBA audit process. A proper pre-audit assessment demands action and input from multiple staff members, including those in the financial offices (Financial Aid Office, Registrar, etc.), security (both physical and digital) and others in information technology. Coordinating and performing such an undertaking will likely involve teaming with an experienced outside partner.
Your organization may already be employing some provisions, such as encryption of sensitive data, limiting and monitoring information access, as well as staff training on security and information security. If not, these practices should be part of your institution’s overall security program.
Other provisions, such as the designation of a qualified individual to oversee an institution’s information security program and the training of security personnel, are aspects that organizations must plan out based on available personnel. While the Safeguards Rule does mandate a qualified individual oversees the GLBA-required security program, this individual may certainly receive assistance (internal or external) in this management.
The provisions for which educational institutions will likely require outside assistance are the performance of risk assessment and the development of an IR plan as part of a comprehensive security program. Even if some aspects already exist within an educational organization, the scope and complexity of the GLBA requirements will likely exceed the time and resources available to a school’s IT staff. Engaging a knowledgeable partner who can perform a comprehensive pre-audit assessment and communicate effectively on risk and mitigation steps is highly recommended – and by doing so – completes one of the audit requirements.
Pre-Audit Risk Assessment
Performing a Risk Assessment should utilize industry-standard security frameworks such as the Center for Internet Security (CIS) Controls or NIST SP 800-171. Use of these frameworks, while not currently obligatory, does represent a best practice when preparing for any cybersecurity audit. The Student Financial Aid Office has suggested Title IV institutions consider using the NIST SP 800-171 framework for risk self-assessment. However, the simplicity of the CIS Controls framework is a viable option that may be a better fit for organizations with less robust security staff. The CIS controls are a straightforward set of 18 controls that provide actionable steps for minimizing data breaches and significantly reducing the risk of cyberattacks.
Using a chosen cybersecurity framework, like NIST or CIS Controls, institutions must conduct a risk assessment across all covered organizational units. Upon risk identification, concise documentation for each safeguard employed is necessary for tracking implementation progress. Risk assessments that meet auditor requirements will address the following:
- Employee security training and management
- Organizational vulnerabilities
- Understanding of threats that might exploit those vulnerabilities
- Creating concise documentation for the actions taken to mitigate all discovered risk
Security Program’s Incident Response Plan
While self-assessment helps identify risks and creates measures for eschewing them, breaches are always possible. Constructing a response plan for security events is vital to passing the audit. In the unfortunate but likely event that a breach occurs, it is critical to have an established plan to handle communications and coordinate investigation, containment and rapidly eradicate the attack. Auditors are looking for institutions to have a security program that includes a written IR plan providing for the following components:
- Identification of types of incidents that could occur, such as data breaches, cyberattacks or natural disasters
- Establishment of an IR team with specific roles and responsibilities
- Procedures for identifying and responding to incidents, including steps for containment and mitigation, preservation of evidence, as well as notification to affected individuals, key stakeholders (including employees, students or parents) and regulatory authorities
- Testing of the IR plan through scheduled drills and exercises
- Periodic review and update of the IR plan that adapts to institutional changes or external threats
- Recording of incidents, responses, outcomes and measures to prevent reoccurrence
Beyond the Assessment
Ultimately the goal is not just to pass the audit through a series of ‘check the box’ exercises but to truly secure data and infrastructure. The GLBA audit process is not just a one-time action but rather a long-term commitment to a series of best practices. To be done correctly requires significant resources and time and involves constant reassessment and adjustments to meet current and future risks.
OneNeck’s experienced team is here to help prepare for GLBA audit compliance and continue working with your technology team to allow your security posture to mature. Our pre-audit services include a requisite risk assessment of security controls that fall under GLBA, assistance documenting your security program and review or development of an IR plan that assists in accurately identifying processes and procedures in the event of an incident.
Contact us to speak to a member of our experienced security team today.
Frequently asked questions…
What happens if you violate GLBA?
Violating the GLBA (Gramm-Leach-Bliley Act) can result in severe penalties, including fines and legal action. The exact consequences depend on the severity of the violation and can range from monetary penalties to imprisonment for individuals found guilty of criminal violations.
What are the three key rules of GLBA?
Firstly, financial institutions must provide customers with privacy notices explaining how they collect and share customers’ personal information. Secondly, customers must be given the option to opt-out of having their information shared with non-affiliated third parties. Thirdly, financial institutions must implement appropriate safeguards to protect customers’ personal information.
Who does the GLBA Safeguards rule apply to?
The GLBA Safeguards rule applies to financial institutions, including banks, credit unions, securities firms, and insurance companies, as well as non-financial institutions, that receive or maintain personal information about customers of financial institutions in connection with providing services to those institutions.
What is the goal of the FTC Safeguards Rule?
The goal of the FTC Safeguards Rule is to protect consumers’ personal information held by financial institutions by requiring them to develop and implement comprehensive information security programs. The rule aims to ensure that financial institutions are taking appropriate measures to safeguard sensitive customer information from unauthorized access, use, or disclosure.
Additional Resources:




