Congratulations You've been Spear-Phished |April Fools!

April 1st is a day marked by good humored pranks, but the internet has changed that significantly; when you get pranked by a cybercriminal, your internet security is compromised, and that’s no joking manner.
Phishing 101
Phishing attacks are one of the most common cybersecurity challenges that organizations face in keeping their information secure, and the latest twist is called spear phishing. Spear phishing, a more targeted form of phishing in which the email appears to come from someone the recipient knows and trusts like a friend, co-worker or even their employer’s human resources department). Before crafting the message, the attacker will research the victim’s social media profiles on LinkedIn, Twitter and Facebook, collecting data to try to build a profile on the victim’s life, work and interests, all in an attempt to acquire sensitive information or credentials.
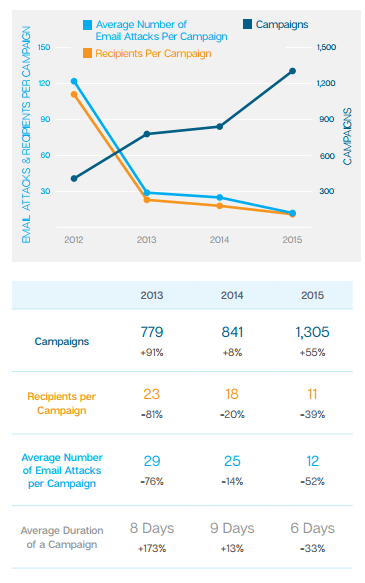
According to the Symantec Internet Security Threat 2016 report, spear-phishing campaigns targeting employees increased 55% in 2015 and is expected to continue to increase.
In addition, the report indicates that in 2015, the number of campaigns increased, while the number of attacks and the number of recipients within each campaign continued to fall. With the length of time shortening, it’s clear that these types of attacks are becoming stealthier.
Stealthier? How? It’s simple, spear-phishing attacks are less likely to arouse suspicion within an organization as the campaigns are smaller, shorter and target fewer recipients.
The end result of a successful spear-phishing attack can be substantial revenue loss or damaged reputation.
Thwarting Attacks
Cybersecurity has become a leading issue in business today. Threats, both internal and external, have the potential to shut your business down if you’re not prepared and updating your security systems and processes on a regular basis.
While there is no cure-all that will put an end to spear-phishing attacks, IT security professionals can focus on shrinking the attack surface. A comprehensive security approach is crucial including network, application, enterprise mobility, and identity and secure access solutions to protect your organization from the internal and external threat landscape.
Once the technical components are in place, it’s imperative to create awareness amongst your employees in regards to spear phishing and the damages these attacks can cause. By providing employees with exactly what to look out for, companies can greatly minimize their risk of falling victim.
OneNeck, a Trusted IT Security Services Provider
At OneNeck, our security services address the broad scope of security and compliance needs that businesses face. We have a depth of experience in assisting our customers with their security needs, and our team is made up of security experts who stay current on the emerging threats so you don’t have to. Contact us today to talk about your security strategy and avoid getting fooled by outside threats.